One day you’re a hero, the next you’re a dog. The shadowy group of (unfortunately) super talented, politically motivated pro-Kremlin hackers known as Killnet found out that’s how life rolls.
Late yesterday afternoon I got a message from our son Ebola in Germany – smack in the middle of all the UFOs and US fighters/tankers over the Great Lake insanity, not to mention word that cable service in half of Philly was out, too – along with a really interesting tweet. It certainly made me wonder if it wasn’t all related somehow.
Would be quite interesting if there is indeed some sort of ongoing DDOS attack interfering with NATO network infrastructure at the moment. Don't usually see this kind of message on ACARS so it's hard to say if that's what's going on.
— IntelWalrus (@IntelWalrus) February 12, 2023
He’d quickly searched for anything more he could find on it, as did I when he passed the info along, and there was nothing for the better part of Sunday evening, U.S. time. Not a peep. As with “decommissioned” octagonal flying objects of unknown origin, no further word was available. In the meantime, I wanted to find out more about who or what this “Killnet” outfit was.
Known for their targeted distributed denial-of-service (DDoS) attacks, Killnet has caused a fair amount of chaos since the Russian invasion of Ukraine, but not so much damage as of yet.
…The attacks — like most Killnet attacks since Russia’s invasion last February — appear to have done little to seriously disrupt network operations at any of the targeted organizations, which included Stanford Health, Michigan Medicine, Duke Health, and Cedars-Sinai.
They’ve been striking out at anyone and any entity that they perceive as actively opposing Russia. Sometimes the targets for these attacks make perfect sense from a “connected to the conflict” angle and other times, they’re head-scratchers. But when one of their DDoS hit, it’s a major pain-in-the-tookus for all concerned and could be deadly.
…”Killnet has been actively attacking anyone who supports Ukraine or goes against Russia for almost 12 months now,” says Pascal Geenens, director of threat intelligence at Radware. “They have been dedicated to their cause and have had the time to build experience and increase their circle of influence across affiliate pro-Russian hacktivist groups.”
Killnet surfaced last year, soon after Russia invaded Ukraine in February. Since then, the group has carried out a series of often high-profile DDoS attacks on organizations in critical infrastructure sectors in the US and multiple other countries. Their victims have included airports, banks, defense contractors, hospitals, Internet service providers, and the White House.
Killnet’s latest DDoS campaign this week against hospitals in the US and medical institutions in multiple other countries, including Germany, Poland, and the UK, were likely motivated by the recent US-led decision by NATO countries to send battle tanks to Ukraine. However, the impact of these attacks remains questionable.
There is also serious concern that the group, nebulous as it may be, is looking to up the ante to more virulent forms of cyber warfare, as DDoS, while annoying and paralyzing at that moment, is usually easily recovered from. The warnings to up security games …
A pro-Russian hacktivist group’s low-level distributed denial-of-service attacks on U.S. critical infrastructure could be a precursor to more serious cyberattacks, health care and security officials warned this week.
…That said, they are likely going to garner Killnet more support from other like-minded hacktivists in Russia and elsewhere, and possibly even fuel investments into its operations from others, making them more dangerous in the process, security experts said this week.
…”While KillNet’s DDoS attacks usually do not cause major damage, they can cause service outages lasting several hours or even days,” the AHA warned. Killnet’s links to Russia’s Foreign Intelligence Service remain unconfirmed, AHA noted, “[but] the group should be considered a threat to government and critical infrastructure organizations, including healthcare.”
Importantly, Killnet’s pro-Russian DDoS crusade has also begun attracting many more followers and fans. Daniel Smith, head of cyber-threat intelligence at Radware, says the number of subscribers for @Killnet_reserve on Telegram grew from about 34,000 subscribers to 85,000 subscribers in June 2022. “Just for comparison, IT Army of Ukraine has over 200,000 subscribers, but has been losing subscribers since March 2022,” he says.
The group has focused quite a bit on publicity via its Telegram channel, which it also uses to encourage followers to conduct DDoS attacks of their own.
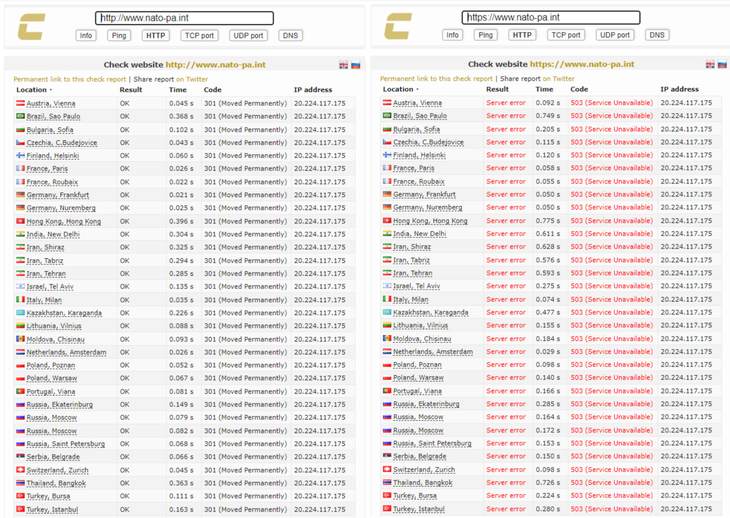
By this morning Ebola was able to send me an article that had broken overnight. Last week Killnet had threatened, and yesterday executed, a DDoS on NATO. For example, they’d managed to shut down NATO’s Parliamentary Assembly homepage. What normally looks like this…
…looked like this for the better part of Sunday.
#NATO websites were hit by a serious cyberattack yesterday but Secretary General Stoltenberg says no classified sites were breached.
Some websites are still experiencing problems. pic.twitter.com/95AV5PhbYc
— Teri Schultz (@terischultz) February 13, 2023
As of 10:22 Central, the link to NATO’s Supreme Headquarters Allied Partners Powers* Europe (SHAPE) [*correction: Beege] on their Structure page is still spinning like a madman. So still inoperable and the attacks are ongoing.
In addition to websites, etc, it turns out the Killnet self-proclaimed freedom-fighting heroes are having to do some furious damage-control tap dancing. Their NATO DDoS also affected and hampered earthquake relief efforts, having jacked with communications between U.S. transports bringing life-saving supplies, medical gear, and personnel into Turkey and Syria. Brilliant PR move, fellas.
Russian hackers have disrupted contact between Nato and military aircraft providing aid to victims of the Turkish-Syrian earthquake which has claimed at least 28,000 lives.
A Nato official confirmed that the alliance had fallen victim to a cyber attack, which is believed to have been carried out by the Killnet group of hackers.
The Killnet group of hackers claimed responsibility for the distributed denial of service (DDoS) attacks but didn’t give any more details.
“We are carrying out strikes on Nato. Details in a closed channel,” it said on one of its associate Telegram channels.
The website of Nato Special Operations Headquarters, which is based in Belgium, was down for only a couple of hours before it was restored.
Other organisations affected by the attack included the Strategic Airlift Capability.
It is a multi-national organisation which relies on Nato support in its task of providing military and humanitarian airlifts.
When questioned about the ACARS (Aircraft Communications Addressing and Reporting System) warning (in the first tweet) to the C-17 in question, NATO confirmed the attack as well as its probable impact on earthquake relief, especially critical in such a volatile area to begin with.
…One of the organisation’s C-17 aircraft, which was believed to be flying supplies to the Incirlik Air Base in southern Turkey, was warned of the disruption in a message from a SAC manager via the ACARS (Aircraft Communications Addressing and Reporting System) network.
The aircraft was told that Nato’s NR network – which is believed to be used for transmitting sensitive data – had been hit by the denial of service attack.
Although contact with the aircraft was not lost, the hackers’ attack is likely to have hampered the relief efforts.
Confirming the hackers’ attack the Nato official said: “NATO cyber experts are actively addressing an incident affecting some NATO websites. NATO deals with cyber incidents on a regular basis, and takes cyber security very seriously.”
The “NR network” they refer to is a secure, restricted network for sending sensitive, unclassified information. The ACARS report was letting the crew know that network was down.
It’s one thing to supposedly be defending Mother Russia’s interests in cyberspace. It’s a whole ‘nuther ballgame when the body count from a catastrophic regional natural disaster in Killnet’s own backyard is fast approaching 40,000 lives lost, there’s no end in sight, and the arrogant jackasses mess with the only competent help coming into the area.
They’re not making any friends. Not used to getting called out, they are pretty angry and, oooh, are they defensive about their own major foul-up. As Ebola sent me,
“Apparently they’re b***hurt they inadvertently hit airlift command’s acars systems.”
If they’re such geniuses, secondary and tertiary effects of actions should be a consideration, no? DERP.
This is an exchange from Killnet’s own Telegram board. You can practically hear the whinging from here. [cue: waah waah]
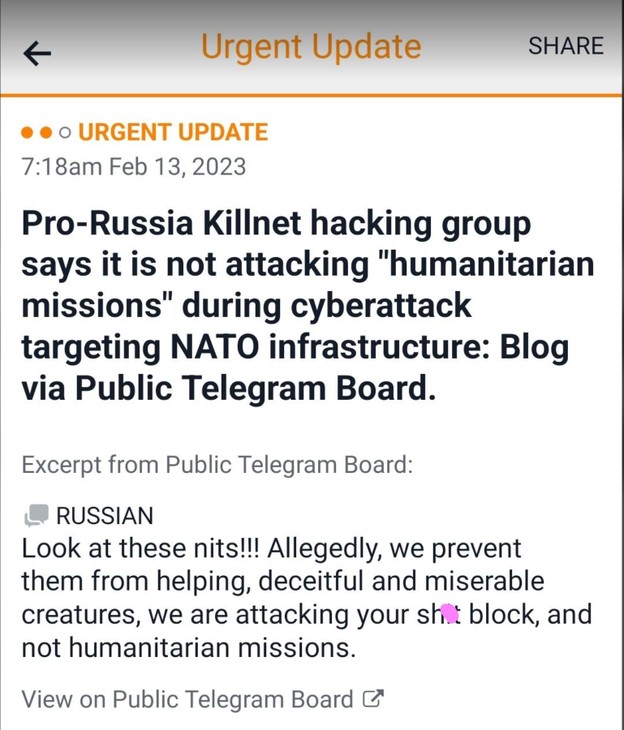
Kicking and screeching they didn’t attack “humanitarian missions” when the whole world can see, hello. They did.
This is not the publicity in that part of the world Killnet wants and man, are they ever getting it anyway. *giggety*
A group of Russian hackers known as #Killnet disrupt contact between #NATO and military aircraft providing aid to victims of the 7.8 magnitude #Turkey-Syria earthquake which has so far claimed over 30,000 lives.https://t.co/zvLQ4tu0ZT
— Al Arabiya English (@AlArabiya_Eng) February 13, 2023
Again, they’re not making any friends and it couldn’t happen to a more worthy bunch.
I haven’t a clue what our counter to all of their efforts is, but obviously, it’s not enough. Though, to be fair, DDoS attacks are so evilly effective in their simplicity that there’s little to be done to ward them off.







Join the conversation as a VIP Member